1000..1100 Terraform Gitops
- how to do operations by pull request
- code fresh + terraform
- Erik Osterman, Cloud Posse http://cloudposse.com $250/hr
- only do evops for companies, terraform company
- Sweetops https://slack.sweetops.com
gitops
- deploy to master and deploy
devops statusquo
- manual rollouts
- poor audit trains
terraform more problems
- IaC
- describe the state of the infrastructure
- not easy to rollback, managing the transition of state
- won’t work well with gitops because if the migration fails, master is not stable
Example
terraform plan
terraform apply
why deploy to production fails?
- too many permutations to keep straight
- helm, terraform, aws accounts, tools, customers, …
- fix: not going to deploy from the developers laptop
- Goal: make it easy for the team
Gitops
- use git as a sytem of record for the desired state of configuration
- operation by pull request for IaC
- use ci/cid for devops
Gitops Objectives
- repeatable, predictable, auditable, accessible
Solution -> codefresh
- https://codefresh.io
- automate anything
- helm, terraform, terragrunt, gitlab, bitbucket, anisible,
- stick everything you want to automate into containers
- string containers together in a pipeline, run them
Basic Flow Diagram
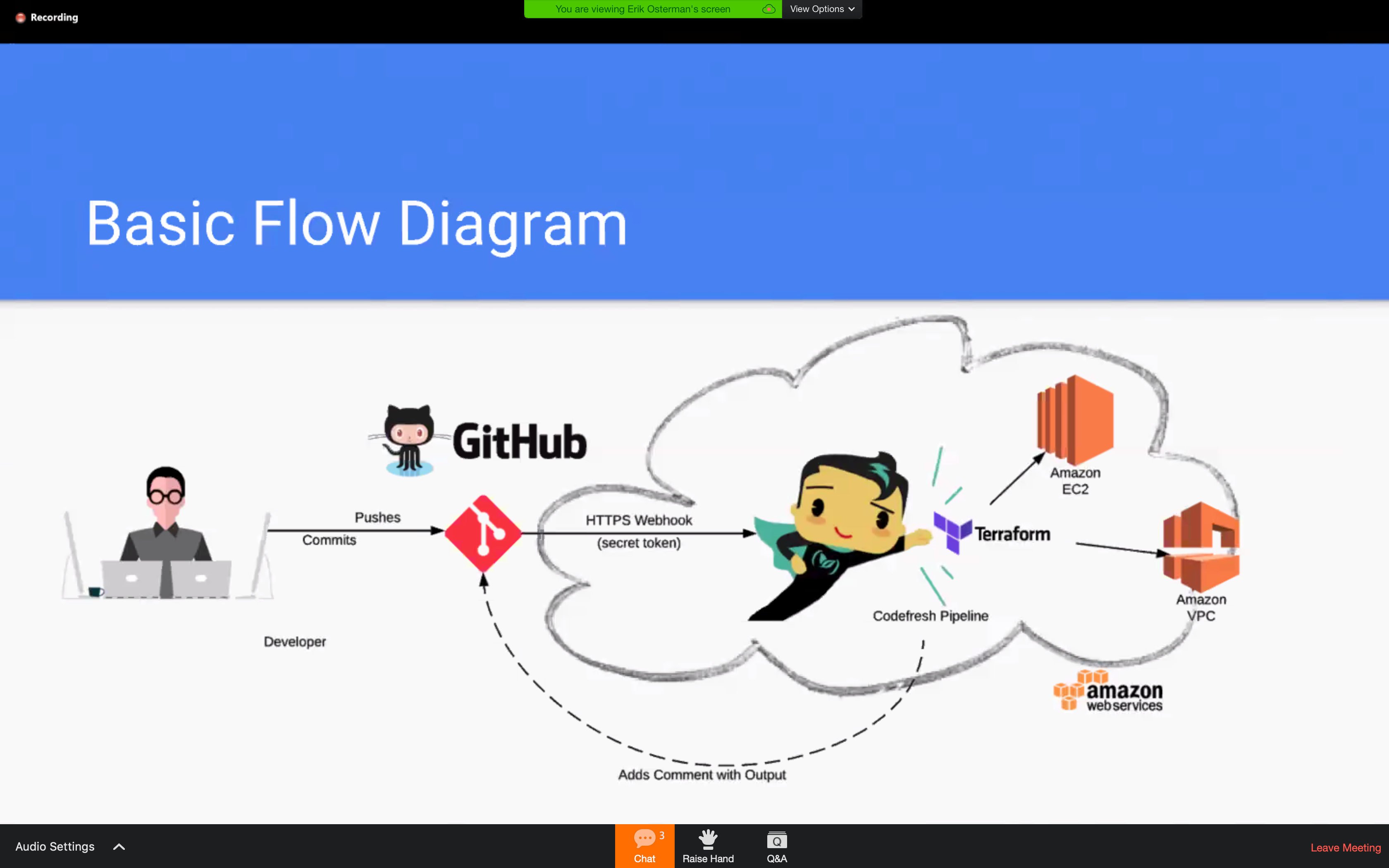
- Open PUll Request
- Review “Auto Plan” => git hook to check it
- Seek Approval
- Deploy Changes
- Merge Pull Request
to get started
- sign up for codefresh
- add codefresh.yaml to each terraform
codefresh.yml sample
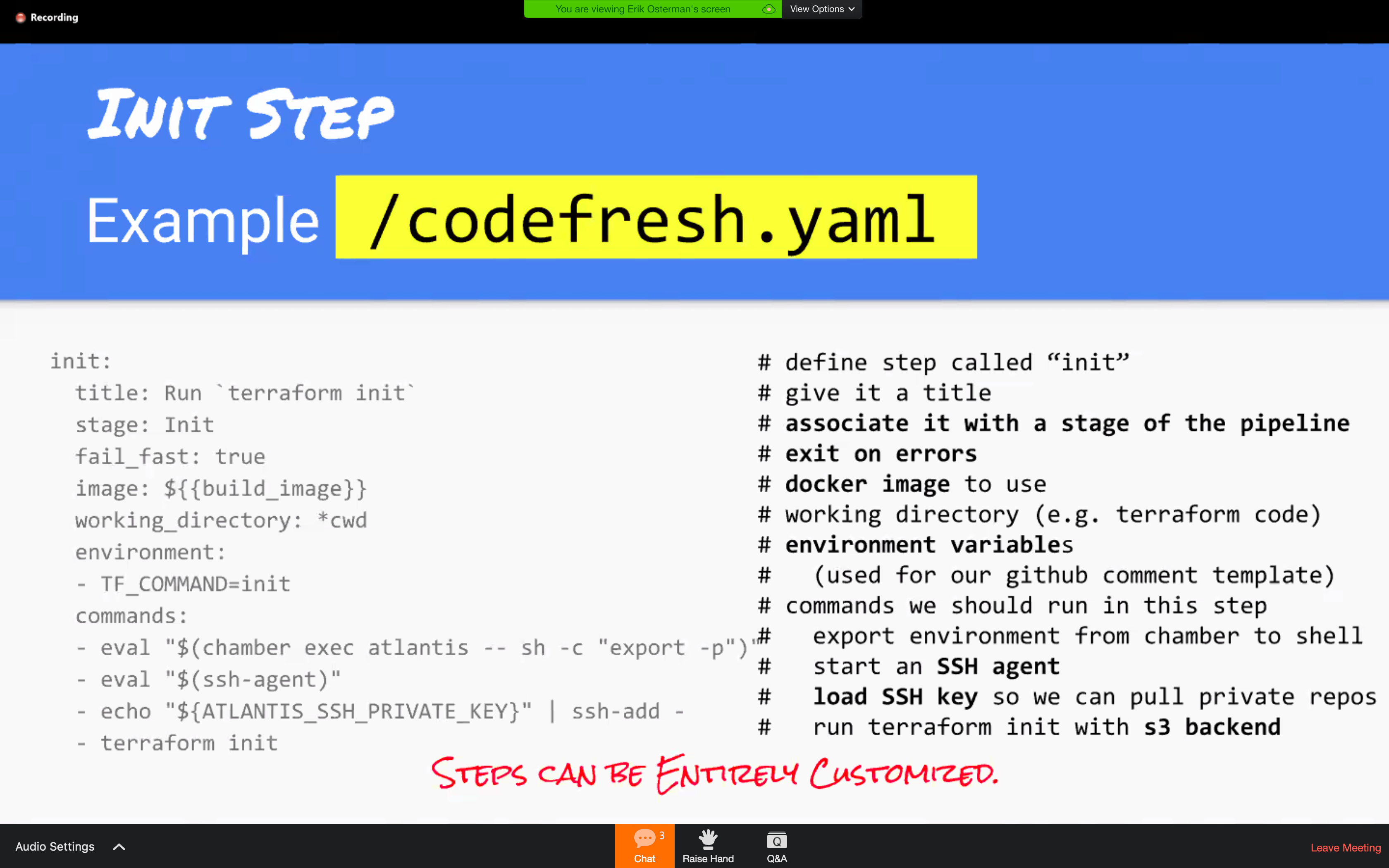
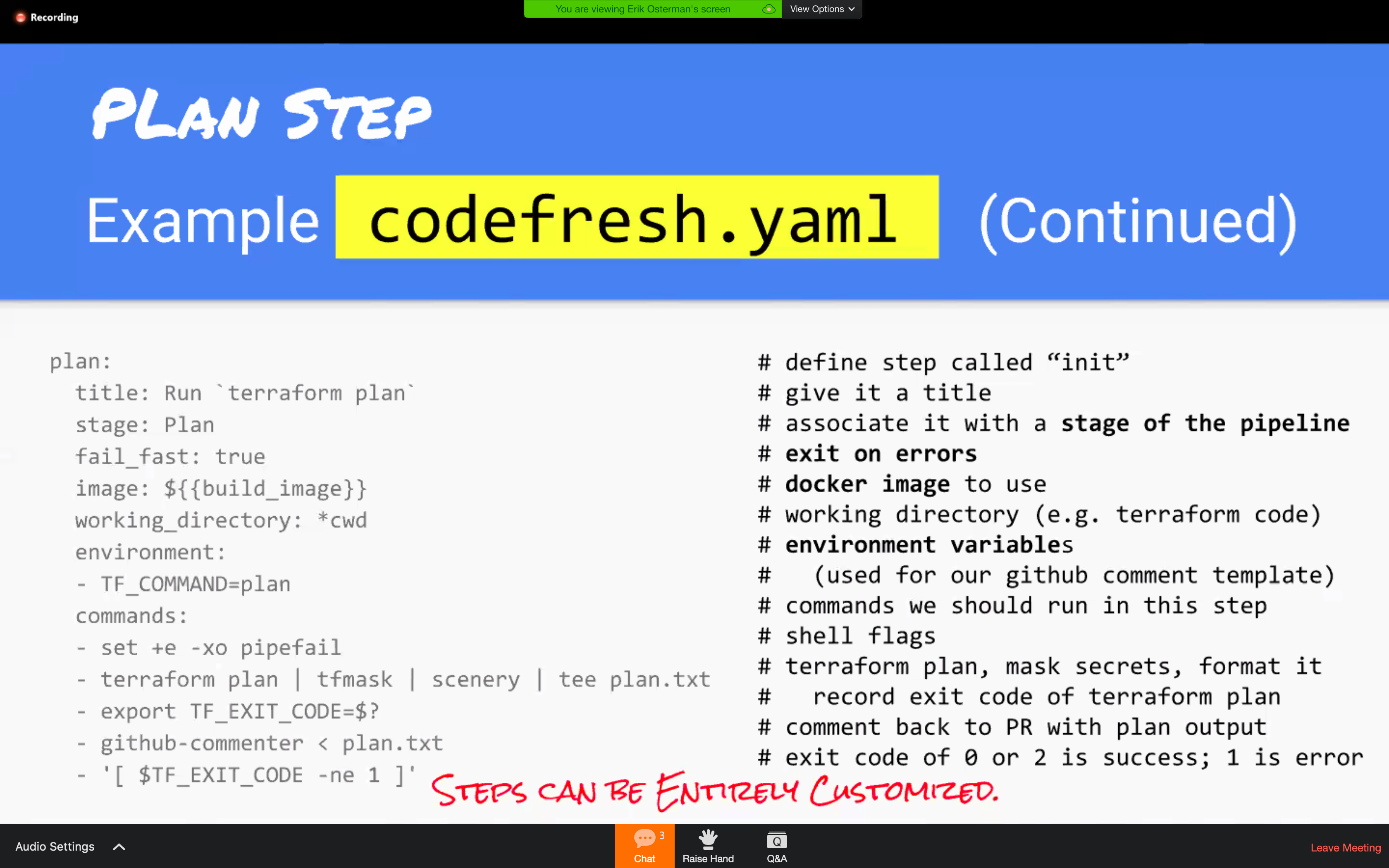
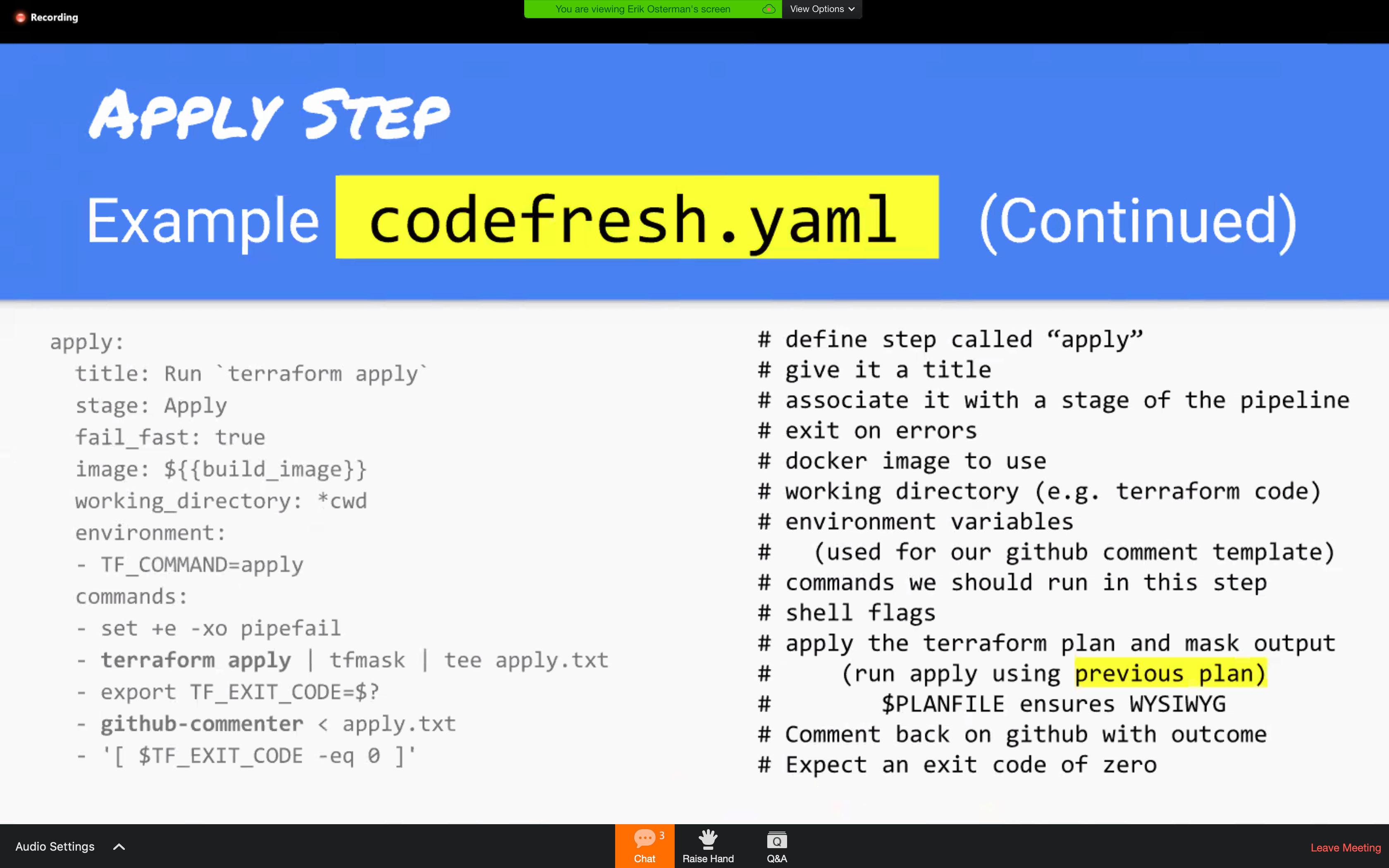 TFmask to filter the secret information from STDOUT
TFmask to filter the secret information from STDOUT
Livedemo
- add user
- open pr
- run plan
- seek approval
- apply
- merge
out best practices
- use geodesic as our cloud automation shell
- use IAM STS for short lived AWS credentials
- use github codeowners
- use .tfvars for non-secrets
- use SSM parameter store + KMS for secrets
- use scenery for clean output
- use tfmask to sanitize output
Links
- cpco.io/codefresh-gitops
- github.com/cloudposse/tfmask
- github.com/cloudposse/geodesic
